by digitaloperatives | Oct 19, 2018 | Research, Services
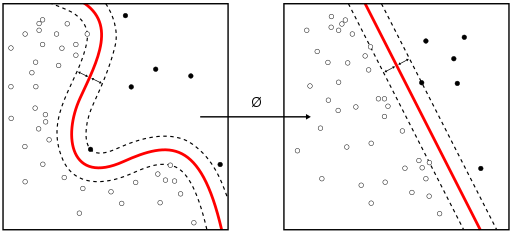
Reading /r/netsec today, I happened to come across this recycled old 2017 blog post from Cisco security about detecting malware by applying machine learning to encrypted communications. Admittedly, it’s an interesting idea. At some point malware started using...
by digitaloperatives | Sep 1, 2018 | Research
At Digital Operatives, sometimes our eyes are bigger than our stomach. We’re a small, focused security company trying to help the nation improve in cyber-security. Fundamentally though, we’re an “ideas” company. We come up with ideas, and as...
by Steve Lavoie | Sep 12, 2017 | Research, Services
How much vulnerability analysis can we automate? How complete, and reliable, are those results? How well can we even answer those questions? Digital Operatives has been exploring questions like these for quite a while and the answer may be “much less than you...
by digitaloperatives | Aug 27, 2017 | Research, Security News
Q: Is this a cyber security story or a finance risk story? A: Both, financial and cyber risks are more related than ever. I’ve read about the reasons for owning Bitcoin, some of these were intuitive for me long before this was ever compiled. Back in 2012 when I...
by digitaloperatives | Jul 5, 2017 | Research
Magiic was created in 2013 to help users securely index and search their PGP-encrypted email. It has been a while since Magiic was released and updated, and its original functionality of indexing only messages stored on a remote IMAP server did not serve...
by Nate | Apr 16, 2015 | Research, Security News, Services
Deoxyribonucleic Acid, or DNA as it is commonly known, has been the gold standard in forensic evidence associated with convicting criminals or overturning convictions that did NOT have, at the time, conclusive DNA evidence. Frontline recently studied some of the...


