by digitaloperatives | Oct 19, 2018 | Research, Services
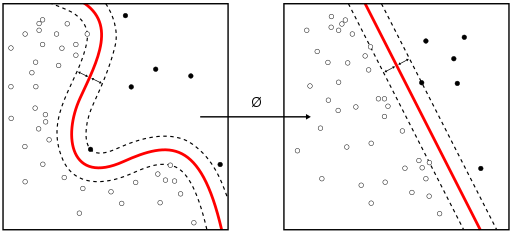
Reading /r/netsec today, I happened to come across this recycled old 2017 blog post from Cisco security about detecting malware by applying machine learning to encrypted communications. Admittedly, it’s an interesting idea. At some point malware started using...

by digitaloperatives | Oct 10, 2018 | Capture the Flag, Security News
On Monday we became a tenant at the shared office provider WeWork. According to their website, “WeWork is a global network of workspaces where companies and people grow together.” We needed something more flexible while our new corporate office is being...




